How Overreliance on EDR Is Failing Healthcare Suppliers
Endpoint Detection & Response (EDR)
,
Endpoint Protection Platforms (EPP)
,
Endpoint Security
Healthcare Suppliers Should Revisit Endpoint Safety to Mitigate Cyberthreats

Ransomware attacks have far-reaching consequences on healthcare organizations, extending well beyond financial losses. A University of Minnesota School of Public Health study found that hospital quantity dropped by 17% to 26% throughout the first week of an assault. Between 2016 and 2021, disruptions from ransomware assaults resulted in an estimated 42 to 67 deaths of Medicare sufferers.
Healthcare suppliers deal with delicate data of hundreds of thousands of individuals, and that makes them a goal. They swim in an ocean of guidelines and laws, and their compliance is consistently scrutinized.
It is simple to overlook – not less than till your subsequent bodily – that chasing compliance and defending sufferers’ knowledge usually are not the highest priorities of healthcare suppliers. These organizations usually maintain one thing extra valuable than our information: They look after our well being. Merely put – they maintain us alive.

How is it then that these organizations – those we flip to within the darkest moments of our lives, the praised first responders when pandemics hit – are featured in cybersecurity information seemingly each different day? And normally not with a hit story.
The reply lies within the calculated decision-making of cybercriminals.
Healthcare Cyber Breaches: A Rising Concern
Healthcare is a major goal for ransomware assaults due to the life-or-death stakes, entry to delicate knowledge, operational disruptions and potential regulatory fallout, making suppliers extra inclined to pay ransoms.
Healthcare organizations have been the goal of greater than 21% of assaults in 2023-2024, up from 18% within the earlier yr, according to analysis by Barracuda Networks. Excessive-profile assaults on organizations together with Change Healthcare, Ascension and MediSecure spotlight the sector’s vulnerability, the place knowledge is usually exfiltrated earlier than being encrypted, exacerbating the dangers.
It is Time to Revisit Our Strategy to Healthcare Cybersecurity
A decade in the past, a hospital made headlines for being hit by ransomware. In response, the hospital head stated he couldn’t justify funding in cybersecurity as a result of “not like a brand new CT scanner,” cybersecurity does not have an effect on affected person outcomes. This did not age effectively. The healthcare business is now acutely conscious that cybersecurity is important for each affected person security and the continuity of care.
Many organizations proceed to rely solely on endpoint detection and response, or EDR, options to fulfill regulatory requirements. However compliant has by no means been a synonym for safe. EDR options are designed to detect particular threats, however their scope is proscribed, making them weak to classy assaults that bypass conventional defenses.
As is usually the case, the satan is within the particulars. Stolen credentials are bought on the darkish internet, customers run as admins, official instruments are used to steal cookies and hijack the online periods, weak multifactor authentication is used and servers sit unprotected as a result of their assault floor is small.
George Kurtz, CEO of CrowdStrike, maybe said it finest in response to a senator’s query throughout congressional hearings in 2021 on the SolarWinds breach: “… Upon getting admin entry on a selected system, if you’re shutting it down, you are able to do just about no matter you need on it.”
EDRs Lack Foundational Controls
Let’s take into account just a few inherent EDR shortcomings that stem from the answer’s focus, risk mannequin and operational mannequin:
- EDR shouldn’t be user-aware. It doesn’t have a method of authenticating the consumer and depends on the working system. Whoever has the password is the proper of consumer for EDR.
- EDR doesn’t differentiate between an administrator and a daily consumer. There are a number of revealed strategies of tampering with EDR with out tripping the wire utilizing elevated entry, akin to eradicating EDR hooks.
- EDR focuses on malicious recordsdata and behaviors. A “official” consumer leveraging official instruments will probably by no means draw consideration.
- Credential theft from the working system, third-party software program and browser credential shops is protected against a malware perspective, whereas entry to LSASS dumps, NTLM hashes, PuTTY recordsdata, cookies and internet session knowledge shouldn’t be universally blocked.
- Customers typing passwords is enterprise as regular for EDR. Keyloggers will probably be discovered and terminated, however extra refined assaults, together with phishing, can leak passwords.
- If attackers efficiently bypassed EDR as soon as, with out correct infrastructure and system hardening, they will return for a second ransom fee.
- Many out-of-the-box detections in EDR techniques usually have to be disabled or excluded in a manufacturing atmosphere false due to false positives attributable to in-house-developed purposes and accepted consumer behaviors that may be tough to distinguish from an attacker’s techniques.
- Complete 360-degree identity security, software management and isolation, robust steady MFA, credential theft safety, role-based least privilege, native administrator account safety and different crucial foundational endpoint safety applied sciences usually are not a part of EDR options.
Stopping Cyberattacks: The Final Protection Technique
Healthcare organizations usually lack the mandatory preventative, identity-centric part of their endpoint safety methods. By incorporating endpoint id safety into their techniques, healthcare organizations can unprivilege the attacker, cut back the endpoint’s assault floor, forestall administrator and common consumer credential compromise and allow an end-to-end passwordless consumer expertise on endpoints. This method permits a safer consumer expertise from login to shopping, minimizing the danger of breaches.
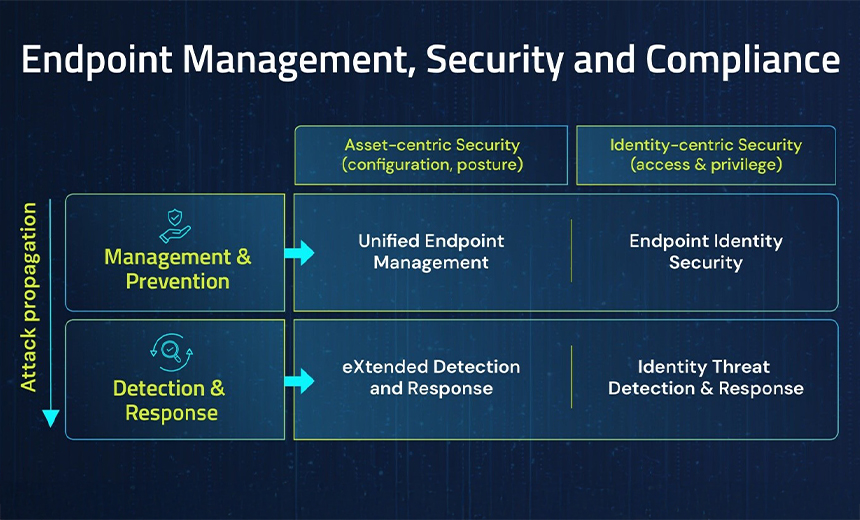
Healthcare Can not Afford to Put All Its Eggs in an EDR Basket
In a defense-in-depth cybersecurity method, EDR, whereas helpful, ought to by no means be the one line of protection. The business should undertake a holistic safety technique that features endpoint id safety as a foundational management. By doing so, healthcare organizations can higher defend their networks, safeguard affected person knowledge and make sure the continuity of crucial companies.
For a deeper dive into this topic, check out our e-book, “Why EDR Is not Sufficient to Cease Cyberattacks.”

