CERT-UA Warns of New Vermin-Linked Phishing Assaults with PoW Bait
The Laptop Emergency Response Group of Ukraine (CERT-UA) has warned of recent phishing assaults that intention to contaminate units with malware.
The exercise has been attributed to a risk cluster it tracks as UAC-0020, which is often known as Vermin. The precise scale and scope of the assaults are presently unknown.
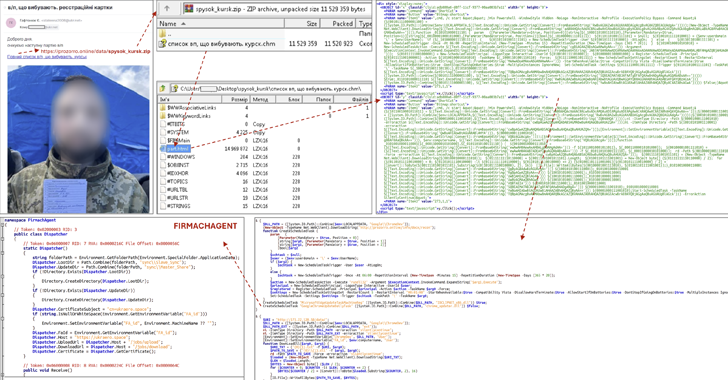
The assault chains begin with phishing messages with pictures of alleged prisoners of battle (PoWs) from the Kursk area, urging recipients to click on on a hyperlink pointing to a ZIP archive.
The ZIP file comprises a Microsoft Compiled HTML Assist (CHM) file that embeds JavaScript code accountable for launching an obfuscated PowerShell script.
“Opening the file installs elements of identified adware SPECTR, in addition to the brand new malware referred to as FIRMACHAGENT,” CERT-UA mentioned. “The aim of FIRMACHAGENT is to retrive the information stolen by SPECTR and ship it to a distant administration server.”
SPECTR is a identified malware linked to Vermin way back to 2019. The group is assessed to be linked to safety companies of the Luhansk Folks’s Republic (LPR).
Earlier this June, CERT-UA detailed one other marketing campaign orchestrated by the Vermin actors referred to as SickSync that focused protection forces within the nation with SPECTR.
SPECTR is a fully-featured instrument designed to reap a variety of data, together with information, screenshots, credentials, and knowledge from numerous on the spot messaging apps like Ingredient, Sign, Skype, and Telegram.