Industrial Distant Entry Software Ewon Cosy+ Susceptible to Root Entry Assaults
Safety vulnerabilities have been disclosed within the industrial distant entry resolution Ewon Cosy+ that could possibly be abused to realize root privileges to the gadgets and stage follow-on assaults.
The elevated entry might then be weaponized to decrypt encrypted firmware recordsdata and encrypted information similar to passwords in configuration recordsdata, and even get appropriately signed X.509 VPN certificates for overseas gadgets to take over their VPN classes.
“This enables attackers hijacking VPN classes which leads to vital safety dangers towards customers of the Cosy+ and the adjoining industrial infrastructure,” SySS GmbH safety researcher Moritz Abrell said in a brand new evaluation.
The findings had been presented on the DEF CON 32 convention over the weekend. Following accountable disclosure, the problems have been addressed in firmware variations 21.2s10 and 22.1s3 as a part of an advisory [PDF] issued by Ewon on July 29, 2024 –
- CVE-2024-33892 (CVSS rating: 7.4) – Info leakage by way of cookies
- CVE-2024-33893 (CVSS rating: 2.1) – XSS when displaying the logs attributable to improper enter sanitization
- CVE-2024-33894 (CVSS rating: 1.0) – Execution of a number of processes with elevated privileges
- CVE-2024-33895 (CVSS rating: 4.4) – Utilization of a singular key to encrypt the configuration parameters
- CVE-2024-33896 (CVSS rating: 3.3) – Code injection attributable to improper parameter blacklisting
- CVE-2024-33897 (CVSS rating: N/A) – A compromised gadgets could possibly be used to request a Certificates Signing Request (CSR) from Talk2m for an additional system, leading to an availability difficulty
Ewon Cosy+’s structure entails using a VPN connection that is routed to a vendor-managed platform known as Talk2m through OpenVPN. Technicians can remotely hook up with the commercial gateway via a VPN relay that happens by way of OpenVPN.
The Germany-based pentest firm stated it was capable of uncover an working system command injection vulnerability and a filter bypass that made it attainable to acquire a reverse shell by importing a specifically crafted OpenVPN configuration.
An attacker might have subsequently taken benefit of a persistent cross-site scripting (XSS) vulnerability and the truth that the system shops the Base64-encoded credentials of the present net session in an unprotected cookie-named credentials to realize administrative entry and in the end root it.
“An unauthenticated attacker can acquire root entry to the Cosy+ by combining the discovered vulnerabilities and e.g., ready for an admin person to log in to the system,” Abrell stated.
The assault chain might then be prolonged additional to arrange persistence, entry firmware-specific encryption keys, and decrypt the firmware replace file. What’s extra, a hard-coded key saved inside the binary for password encryption could possibly be leveraged to extract the secrets and techniques.
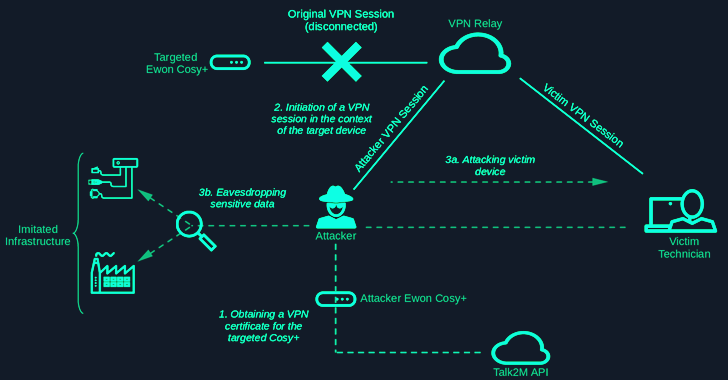
“The communication between the Cosy+ and the Talk2m API is completed through HTTPS and secured through mutual TLS (mTLS) authentication,” Abrell defined. “If a Cosy+ system is assigned to a Talk2m account, the system generates a certificates signing request (CSR) containing its serial quantity as frequent identify (CN) and sends it to the Talk2m API.”
This certificates, which might be accessed through the Talk2m API by the system, is used for OpenVPN authentication. Nonetheless, SySS discovered that the only reliance on the system serial quantity could possibly be exploited by a risk actor to enroll their very own CSR with a serial quantity if a goal system and efficiently provoke a VPN session.

“The unique VPN session will likely be overwritten, and thus the unique system just isn’t accessible anymore,” Abrell stated. “If Talk2m customers hook up with the system utilizing the VPN shopper software program Ecatcher, they are going to be forwarded to the attacker.”
“This enables attackers to conduct additional assaults towards the used shopper, for instance accessing community companies similar to RDP or SMB of the sufferer shopper. The truth that the tunnel connection itself just isn’t restricted favors this assault.”
“For the reason that community communication is forwarded to the attacker, the unique community and programs could possibly be imitated with a purpose to intercept the sufferer’s person enter such because the uploaded PLC packages or comparable.”
The event comes as Microsoft uncovered a number of flaws in OpenVPN that could possibly be chained to realize distant code execution (RCE) and native privilege escalation (LPE).
(The story was up to date after publication to incorporate extra particulars in regards to the CVE identifiers and the supply of the patches.)